Introduction
Check out our second status update for 2026! 👀
BorrowSanitizer is a dynamic analysis tool for detecting Rust-specific aliasing bugs in multi-language applications.
The Rust compiler provides powerful, static safety guarantees by restricting aliasing and mutability. However, developers can bypass these restrictions by using a subset of
unsafe features. These features are necessary for Rust to interoperate with other languages. However, if developers use unsafe code incorrectly, then they can break the rules of Rust’s aliasing model, which the compiler relies on to be able to optimize programs. Incorrect optimizations can introduce security vulnerabilities.
Rust developers can find aliasing bugs using Miri, an interpreter. Miri is the only tool that can find violations of Rust’s latest Tree Borrows aliasing model, but it cannot find these bugs in foreign code. Miri is also significantly slower than native execution, which makes it impractical to use techniques like fuzzing or property-based testing to find these Rust-specific bugs.
BorrowSanitizer is an LLVM sanitizer for finding aliasing violations. Our goal is for it to be fast enough for use with fuzzing tools and to have support for Rust, C, and C++ in interoperation. We intend for it to be a production-ready tool.
🚧 Our project is still in early stages. BorrowSanitizer is not functional yet. 🚧
Join our Zulip if you are interested in contributing or if you have any additional questions about our project. You can build and test our sanitizer by following the setup instructions in the next section. All of our code is open-source and publicly available on GitHub.
Setup
The easiest way to try BorrowSanitizer is inside a Docker container. Our image supports the following platforms:
| Platform | Target | Description |
|---|---|---|
linux/amd64 | aarch64-apple-darwin | ARM64 macOS (M-series) |
linux/arm64 | x86_64-unknown-linux-gnu | X86 Linux |
First, pull our latest image from GitHub’s container registry.
docker pull ghcr.io/borrowsanitizer/bsan:latest
Then, launch a container and attach a shell.
docker run -it bsan:latest
Once inside the container, you can use our Cargo plugin to build and test crates using BorrowSanitizer.
cargo bsan test
Our plugin supports most of the same subcommands as Miri. When it’s used for the first time, it will perform a one-time setup step of building an instrumented sysroot. You can trigger this step manually using the setup subcommand.
Building from Source
Every single command needed to build, test, and install BorrrowSanitizer can be accessed through xb, our build script. For first-time setup, run:
xb setup
If you only want to install BorrowSanitizer, then run:
xb install
This will install a custom Rust toolchain under the name bsan. You can speed this up by building our dev container, which already has the bsan toolchain installed. We recommend using the container to avoid any environment-specific issues.
You can build and test components of the project using the build and test subcommands. For example, running xb build will build everything, but you can also pass the name of a subdirectory to build just that component, like so:
xb build bsan-rt
Nearly every subcommand can be used this way.
After making a change, you should run all of our CI steps locally using:
xb ui
This will place our binaries into Cargo’s home directory ($HOME/.cargo). You will need to have bsan set as the active toolchain (e.g. rustup default bsan) for our tool to work.
Status Update - January 2026
Rust provides static safety guarantees by restricting aliasing and mutability. Rust’s borrow checker enforces these rules for safe code, but programs that use Rust’s “unsafe” operations can easily break them, causing subtle safety errors.
Until now, the primary way to find these bugs was Miri, an interpreter. Miri is precise, and it’s the only tool that can fully validate programs against Rust’s latest Tree Borrows aliasing model. However, it is also quite slow, and it cannot “see” into C and C++ code to detect aliasing bugs that span language boundaries.
BorrowSanitizer is our solution: an LLVM-based sanitizer that instruments programs during compilation. It’s like AddressSanitizer, but for checking programs for Tree Borrows violations. It’s designed to be fast enough for fuzzing and capable of tracking pointer “provenance” metadata—even when code crosses over into C or C++.
Where we stand in January 2026
We are transitioning from a research prototype to a functional tool. While the core logic is sound, we are still focused on three major engineering challenges: integrating with the Rust compiler, making the runtime fast enough for production use, and tracking pointer metadata in multithreaded programs. We have been testing BorrowSanitizer using the single-threaded programs from a subset of Miri’s test suite that deals with aliasing violations, and we have similar outcomes; tests either pass or report an error in both Miri and BorrowSanitizer. Once these features are merged, we will be able to expand our support to the rest of Miri’s tests, and we will begin auditing failing tests to make sure that we are finding the same errors as Miri. We will begin automated testing and benchmarking on real-world libraries, and you can expect to see benchmarking results in our February update.
We discuss these points in more detail below. We will continue to post monthly updates here and in our project goal.
Compiler Changes
Retags are the central mechanism of Tree Borrows. Broadly, when a reference is created, assigned, or passed into a function, its underlying pointer is “retagged”. This creates a new permission that’s recorded in a tree of permissions associated with the allocation being accessed. Miri uses a combination of type information and explicit
Retag instructions to determine when a retag needs to happen, but all of this information is lost at the LLVM level. Ordinarily, this would prevent us from distinguishing between raw pointers and references, and we need to do this to be able to find aliasing violations.
We modified the Rust compiler to emit retags as function calls. If we have the following MIR:
x = &mut y;
We emit the following function call:
%2 = @__retag(ptr %1, ...)
We use a fork of the compiler with a prototype of these changes in our current implementation of BorrowSanitizer.
In December, we posted a pre-RFC describing these changes, which was adapted into the MCP that we posted earlier this week. Our current prototype depends on MIR
Retag instructions to determine where to emit retags during codegen, but these instructions are likely going away, so the final version of our changes will determine where to insert these instructions during codegen. We expect these changes to be relatively straightforward, so barring any unexpected concerns, we should be able to merge our changes before the start of the second project goal period in April.
Once these changes are merged, the rest of development can continue out-of-tree. However, there’s another relevant proposal that would be helpful to have implemented to support BorrowSanitizer. Last September, an MCP was accepted for including clang as a Rust component. Our instrumentation pass relies on the distribution of LLVM that’s bundled with nightly, so we need clang to have a matching version to be able to instrument C and C++ programs. Having clang as part of the user’s sysroot would make this far easier.
Remaining features
Three critical features have yet to be finished before we can expand our testing to the rest of Miri’s test suite and more real-world crates. The following list is not comprehensive—there are other features that we have yet to support, such as thread-local storage, global variables, and constant allocations. However, we expect that these will be straightforward extensions of existing functionality, and not core features like the following:
Error Reporting
When Miri finds an aliasing violation, it reports both the primary location where the error occurred and the secondary locations of memory accesses that indirectly caused the error. It’s relatively straightforward to provide a backtrace for the primary location, and we can record the instruction pointers for the secondary locations within the nodes of the tree. However, we have not implemented a method for translating these instruction pointers into source locations. We are currently adding support for using
llvm-symbolizer to handle this, and once it is finished, we will introduce nicer error messages so that we can start auditing failing test cases.
Garbage Collection
Periodically, Miri “stops the world” and collects all of the permissions associated with pointers stored in memory. Then, it visits the stack or tree for each allocation and removes permissions that are no longer reachable in memory. This can dramatically improve performance.
Like Miri, we can scan our shadow memory spaces for provenance values. However, instead of halting execution, BorrowSanitizer’s approach will continue to allow threads to execute. A thread will only be blocked when it attempts to update shadow memory. All other operations, including certain run-time checks, will still be able to continue concurrent to garbage collection.
We can already scan through our “shadow heap”, which contains provenance values that are stored to memory. However, we still need a way to track which provenance values are accessible on the stack. At the moment, we load provenance into virtual registers, just like any other LLVM value. This is convenient to implement, but it prevents us from knowing where provenance is stored at run-time. At the moment, we are switching to using a “shadow stack” to store provenance values. Garbage collection will block any operations that update the shadow stack pointer.
Thread-Safe Pointer Updates
Each pointer has a provenance value, which identifies its permission to access memory. Each provenance value is three words: an allocation ID, a borrow tag, and a pointer to an allocation metadata object. Every regular load or store of a pointer requires three additional loads: one for each component of its provenance. These accesses are subject to data races, but that’s acceptable, since any race on a provenance value would also be a race on the pointer’s value. That would be a problem for ThreadSanitizer to detect.
We cannot use the same approach for atomic pointer operations. If we atomically stored each component of a provenance value in succession, then this would not guarantee that all three values would be read consistently as a unit. Our instrumentation would be introducing a data race that does not exist in the original program. When provenance values are read in an inconsistent state, this all but guarantees a false positive error.
We have two options to address this. The easiest approach would be to block shadow memory on atomic accesses. This is expensive, but we can mitigate it somewhat by only blocking the region of memory that is being accessed. Another option would be to remove allocation IDs from our provenance values altogether and use the allocation info pointer as an ID instead. In that case, provenance values would be 128 bits, which is small enough for atomic loads and stores. Support for atomic operations on 128-bit integers is inconsistent but improving, and it could be worth the performance increase.
Evaluation
We do not have a clear idea of what performance looks like yet—we’ve been focused on feature implementation over benchmarking. We are slower than Miri for certain programs at the moment. We can attribute this to our lack of garbage collection and our eagerness in locking global state to validate accesses. Expect to see initial benchmark results in our February update. Additionally, one of our team members—@Gitter499—has been working on a dashboard to display performance results that we can integrate into CI. We also plan on running an instance of Crater once we figure out a configuration that works with our driver.
Conclusion
Let us know if you have any questions! You can reach us on Zulip. Otherwise, you’ll hear from us again in February for our next update.
We thank Google and the Rust Foundation for funding this project, as well as @RalfJung and Tyler Mandry for their time and effort in providing feedback.
Status Update - February 2026
By Ian McCormack and Molly MacLaren
We are building BorrowSanitizer: an LLVM-based instrumentation tool for finding violations of Rust’s aliasing model in multilanguage applications. If you are new to the project, then we recommend checking out our introduction and our first status update before you continue.
February has been busy! This month, we:
- Implemented detailed error messages.
- Gained a better understanding of our performance.
- Improved our integration with LLVM.
We also proposed a 2026 Rust Project Goal for transitioning BorrowSanitizer from a research prototype into a usable tool.
Error Messages
When BorrowSanitizer detects an aliasing violation, its error messages now include snippets of the source code that triggered the error. This moves us closer to error message styling consistent with the format used by Miri and the Rust compiler. For example, here’s what BorrowSanitizer prints when it detects an error in one of Miri’s test cases.
error: Undefined Behavior: read through <TAG>(unprotected) at ALLOC[0x0] is forbidden
help: the accessed tag <TAG>(unprotected) has state Disabled which forbids this read
help: the accessed tag <TAG>(unprotected) was created here, in the initial state Frozen
--> bsan/tests/miri-tests/fail/both_borrows/alias_through_mutation.rs:6:14
|
6 | *x = &mut *(target as *mut _);
|
help: the accessed tag <TAG>(unprotected) later transitioned due to a foreign write
--> bsan/tests/miri-tests/fail/both_borrows/alias_through_mutation.rs:15:5
|
15 | *target = 13;
|
help: this transition corresponds to a loss of read permissions
backtrace:
0:
bsan/tests/miri-tests/fail/both_borrows/alias_through_mutation.rs:16:16
1:
RUSTLIB/core/src/ops/function.rs:250:5
2:
RUSTLIB/std/src/sys/backtrace.rs:166:18
Performance
We want BorrowSanitizer to provide both better FFI support and better performance than Miri. We have plenty of anecdotal evidence that Miri can run upwards of 1000x slower than native execution in certain situations. However, we are still missing the kind of detailed evaluation that we need to identify the root causes of Miri’s overhead and potential areas for optimization. This will help inform our design for BorrowSanitizer, which extends Miri’s existing Tree Borrows implementation.
We are collaborating with Shinhae Kim from Cornell to profile Miri on test cases from the most popular crates. He’s advised by Saikat Dutta and Owolabi Legunsen. We are using Perf, two of Valgrind’s built-in profilers (DHAT and Callgrind), and Miri’s existing tracing macros. Profiling data allows us to track the time that we spend within each of Miri’s functions, its memory usage, and the number of instructions executed. Miri’s tracing logs can provide aliasing model-specific metrics, such as the number of memory allocations tracked and the number of nodes visited within the tree for each allocation. We are currently focused on evaluating Miri under different configurations, but we will be able to add BorrowSanitizer to this benchmarking pipeline in the future.
We were also able to shrink BorrowSanitizer’s provenance metadata, which should help improve performance. At run-time, we originally associated every pointer with an allocation ID, a “borrow tag” identifying its access permission, and a pointer to a metadata object. This took up three words, which is too large for atomic memory accesses. We were able to remove the allocation ID without affecting precision. This will make provenance small enough to load and store with 128-bit atomic operations.
In our initial testing, we noticed that BorrowSanitizer ran significantly slower than Miri for an empty crate, without any tests. Any runtime overhead had to be coming from Rust’s libtest harness, or the prelude. Our logs indicated that BorrowSanitizer was emitting nearly four times as many retags as Miri for the same program. At first, we thought that this was a bug. It seemed like we should have had strictly fewer retags than Miri, since we skip retagging after plain assignments. However, many of the functions that triggered the majority of BorrowSanitizer’s “extra” retags were not being executed by Miri. It turns out that libtest has a “fast path” for Miri:
#![allow(unused)] fn main() { /// Creates a TermInfo for the named terminal. pub(crate) fn from_name(name: &str) -> Result<TermInfo, Error> { if cfg!(miri) { // Avoid all the work of parsing the terminfo (it's pretty slow under Miri), and just // assume that the standard color codes work (like e.g. the 'colored' crate). return Ok(TermInfo { .. }); } ... } }
There are also certain features (like signal handlers) that Miri does not support, but we do. We are not able to use --cfg=miri to get around this, since we cannot guarantee that Miri’s configuration will work for native instrumentation, or vice versa. This makes it tricky to have a perfectly fair comparison between the tools.
We do not have enough data to be confident about BorrowSanitizer’s performance overhead yet. However, there’s an interesting test case from
hashbrown that is still worth taking a look at. The unit test
test_lots_of_insertions is notoriously slow in Miri; it’s even disabled by default, using #[cfg(not(miri))]. Broadly, this test does exactly what it says: it inserts and removes lots of entries from a single HashMap instance. Krit, one of our collaborators, created a variant of this test that lets us control the number of entries (N) being inserted on each iteration of its inner loop. The original test from hashbrown uses N=1000. Here are results for N=1 using BorrowSanitizer, AddressSanitizer, ThreadSanitizer, and both debug and release builds. Measurements are displayed as the average of 100 iterations.
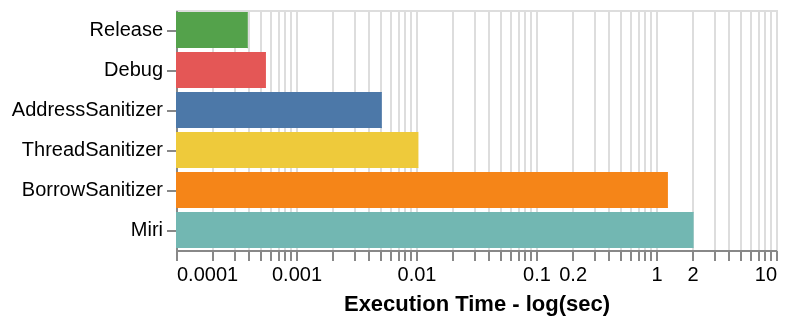
We disabled most of Miri’s checking and nondeterminism, enabled Tree Borrows, and disabled the garbage collector, since BorrowSanitizer does not support garbage collection yet. You can double-check our benchmarking configuration and raw dataset here. This is not an entirely fair comparison. In addition to the limitations surrounding Miri’s compilation directives, our timing measurements include the invocation of the cargo plugins for both Miri and BorrowSanitizer, which work differently. BorrowSanitizer does not instrument global, thread-local, or constant allocations. Since this is a single test case, our results are not representative of how each of these tools performs in every situation. That said, BorrowSanitizer does appear to be significantly faster than Miri (note the logarithmic scale), but both tools are in a similar category of performance here. We have also noticed that BorrowSanitizer tends to be a bit noisier than Miri, but we are not sure why.

These results indicate that BorrowSanitizer’s overall performance is still quite dependent on the performance of Miri’s Tree Borrows implementation. However, BorrowSanitizer still has plenty of room for optimization, since we have mostly focused on feature support up to this point.
LLVM Integration
We have a tentative plan for upstreaming BorrowSanitizer this year. We also improved our integration with the LLVM toolchain by overhauling our “retag” intrinsics, which tell us when new references are created at the LLVM level.
Upstreaming
We will start the work required for upstreaming an experimental version of BorrowSanitizer this year as part of our Project Goal. This process will need to begin with the parts of the tool that have to live inside LLVM. This means that we need to be able to test BorrowSanitizer entirely within the LLVM project’s source tree, which disallows any Rust dependencies. To support this, we are splitting our runtime into two components: an LLVM component and a Rust component. The LLVM component will define BorrowSanitizer’s outermost API. It also implements the parts of shadow memory management and error reporting that rely on LLVM’s
compiler-rt libraries. On its own, the LLVM runtime will effectively be a no-op. But, when the Rust runtime component is linked in, it will override several weak symbols within the LLVM runtime, effectively “enabling” our checking. The Rust component will define everything that is specific to Rust’s aliasing semantics, and we intend for it to live as part of Rust’s source tree.
We will start the RFC process for the LLVM component this spring, once we finish stabilizing our API. Any progress on merging the Rust component will start later this year, depending on the status of our 2026 Project Goal proposal and the requirements from our stakeholders on the Rust Team.
Retag Intrinsics
BorrowSanitizer relies on inserting special “retag” intrinsic calls into programs as they are compiled to LLVM. This is the subject of our current Project Goal and our ongoing MCP. This month, we made significant changes to what retags look like and where they are emitted, so that we can maintain compatibility with LLVM’s noalias metadata.
We originally planned on handling every kind of retag using a single intrinsic function. Consider the following MIR statement:
#![allow(unused)] fn main() { x = &mut y; }
Usually, we would not see any distinction between the variables x and y at the LLVM level. Both would be collapsed into a single SSA variable (or “virtual register” in LLVM terminology). Our retag intrinsics preserve each alias:
%x = call ptr @__rust_retag(%y, ..)
This works great if the pointer being retagged is already available in a register. However, sometimes we need to retag a pointer that is stored at another memory location. Consider the following function:
#![allow(unused)] fn main() { fn example<'a, T>(value: Foo<'a, T>) { .. } }
The lifetime 'a indicates that Foo contains a reference. Reference-type parameters receive a special “function-entry” retag. Depending on the architecture that we are compiling for, value might be passed to the function example using a pointer. Here’s what the LLVM IR would look like in that case:
define void @example(ptr %0) { .. }
In this situation, we need to load the field that contains the reference to be able to retag it. After we finish the retag, we need to store the new alias back into the original location.
%1 = getelementptr ... %0
%2 = load ptr %1
%3 = call ptr @__rust_retag(%2, ..)
store ptr %3, ptr %1
Retagging does not affect a pointer’s address, but it does change its provenance. Every time we update the value of a pointer, we need to update its provenance metadata at the corresponding “shadow” memory location. The store tells our instrumentation pass to update the provenance for the location pointed to by %1 with the provenance of the pointer %3.
However, this additional store caused issues for parameters with LLVM’s readonly metadata annotation. In our example, if the parameter %0 has this annotation, then all write accesses to pointers derived from %0 are undefined behavior and will be removed during compilation—even if we disable optimizations in LLVM.
To get around this, we had to switch to using two different forms of retag. If the pointer being retagged is available in a register, then we use __rust_retag_reg, which has the same semantics as the original __rust_retag shown above. If we need to load the pointer from memory, then we use the form __rust_retag_mem. For the function example, we would see the following LLVM IR:
%1 = getelementptr ... %0
call ptr @__rust_retag_mem(%1, ..)
Our instrumentation pass inserts the necessary load from %1, as well as all of the other shadow memory accesses that we need to update the provenance at this location. Only the provenance changes, and not the address, so we never actually need to write directly to %1.
The other parameters to the retag intrinsic are the same in both of its forms. However, we made a key change to these parameters that will make it easier for BorrowSanitizer to be merged upstream. Originally, retags had a “permission type” parameter (an i64) which was determined by a Rust compiler plugin. To compile a program with BorrowSanitizer, we had to use our special cargo-bsan plugin, which would call a secondary bsan-driver plugin to inject our retag permission type values into rustc. We can avoid this rigmarole by passing the information that we need to determine the “permission type” value as parameters to the intrinsics. Then, we compute the permission type at run-time.
Retagging on Assignment
We also had to change where retags are emitted, which has a subtle effect on the types of undefined behavior that BorrowSanitizer can detect. Miri retags the target of every assignment statement involving a reference—even for assignments that do not explicitly create new references. This means that the following program (from Miri’s test suite) has undefined behavior :
#![allow(unused)] fn main() { let x = &mut 42; let xraw = x as *mut _; let xref = unsafe { &*xraw }; let xref_in_mem = Box::new(xref); // Writing through `xraw` invalidates // the read-only permission of `xref` unsafe { *xraw = 42 }; let _val = *xref_in_mem; }
The last line of this program is what triggers the error. After we load xref from *xref_in_mem, we need to retag it, which performs a read access. However, the reference xref was invalidated by the write through xraw—it no longer has the permission to access anything, so this retag is undefined behavior.
This is unexpected. We are not using _val for anything, and the read access for *xref_in_mem is completely fine. The point that triggers the error in this program is somewhat invisible, but it is still undefined behavior under both Stacked and Tree Borrows. It is not clear yet whether this pattern should be undefined behavior, but for now, it’s an error.
The AddRetag pass excludes certain temporary assignment statements from retagging. We originally used Rust’s MIR
Retag statements to determine where to emit our LLVM retags, so we were able to skip these temporary retags, too. However, it seems like Miri might be moving toward removing retag statements. In anticipation, we decoupled our LLVM retags from Rust’s MIR retags. Instead of relying on the
AddRetag MIR pass, we decide where to emit a retag during codegen. However, the distinction between temporary and non-temporary assignments is lost once we reach codegen, which prevents BorrowSanitizer from skipping retags for temporary assignments.
We have chosen to skip emitting retags after assignment statements. This means that BorrowSanitizer does not report an error for the program above. We still emit a retag when a reference is created and at function boundaries. So far, this does not seem to have had a significant impact on our precision, and it seems possible that Rust’s aliasing model will change to accept these programs in the future. Some differences between BorrowSanitizer and Miri are to be expected, anyway, and this is one that we can live with for now.
Conclusion
Thanks for taking a look! We’ll be back in March with our next status update. In the meantime, you can reach us on Zulip.
About
If you have questions or are interested in contributing, the best way to reach us is on Zulip. You can also send us an email and one of our team members will follow up with you. BorrowSanitizer is open source and publicly available on GitHub.
Talks & Publications
We presented our work at the following venues:
Team
Please reach out to us if you are interested in contributing to this project. Current and past contributors include (in no particular order):
- Ian McCormack
- Oliver Braunsdorf
- Aaron Tan
- Johannes Kinder
- Jonathan Aldrich
- Joshua Sunshine
- Rafayel Amirkhanyan
- Molly MacLaren
- Krit Dass
License & Credits
BorrowSanitizer is dual-licensed under Apache and MIT.
Zulip sponsors free hosting for BorrowSanitizer. Zulip is an organized team chat app designed for efficient communication.